

There are two most important methods to get well encrypted knowledge in a ransomware assault: restoring from backups and paying the ransom. Compromising a corporation’s backups allows adversaries to limit their sufferer’s capacity to get well encrypted knowledge and dial-up the strain to pay the ransom.
This evaluation explores the impression of backup compromise on the enterprise and operational outcomes of a ransomware assault. It additionally shines gentle on the frequency of profitable backup compromise throughout a spread of industries.
The findings are based mostly on a vendor-agnostic survey commissioned by Sophos of two,974 IT/cybersecurity professionals whose organizations had been hit by ransomware within the final 12 months. Carried out by impartial analysis company Vanson Bourne in early 2024, the research displays respondents’ experiences over the earlier 12 months.
Govt abstract
The evaluation makes clear that monetary and operational implications of getting backups compromised in a ransomware assault are immense. When attackers reach compromising backups, a corporation is nearly twice as prone to pay the ransom and incurs an total restoration invoice that’s eight instances greater than for these whose backups are usually not impacted.
Detecting and stopping malicious actors earlier than your backups are compromised allows you to scale back significantly the impression of a ransomware assault in your group. Investing in stopping backup compromise each elevates your ransomware resilience whereas additionally decreasing the general Complete Value of Possession (TCO) of cybersecurity.
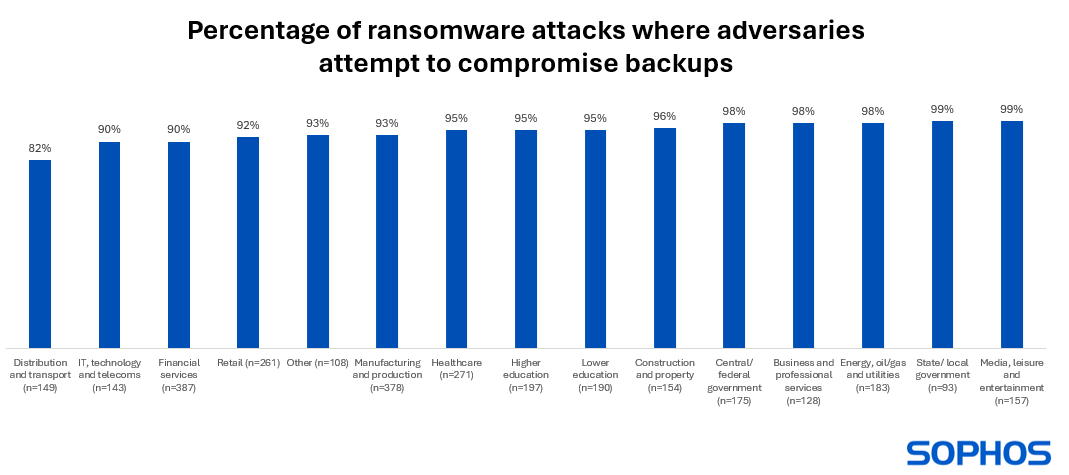
Studying 1: Ransomware actors nearly at all times try and compromise your backups
94% of organizations hit by ransomware previously 12 months mentioned that the cybercriminals tried to compromise their backups throughout the assault. This rose to 99% in each state and native authorities, and the media, leisure and leisure sector. The bottom fee of tried compromise was reported by distribution and transport, nevertheless even right here greater than eight in ten (82%) organizations hit by ransomware mentioned the attackers tried to entry their backups.
Studying 2: Backup compromise success fee varies drastically by trade
Throughout all sectors, 57% of backup compromise makes an attempt had been profitable, which means that adversaries had been in a position to impression the ransomware restoration operations of over half of their victims. Curiously, the evaluation revealed appreciable variation in adversary success fee by sector:
- Attackers had been most definitely to efficiently compromise their victims’ backups within the power, oil/fuel, and utilities (79% success fee) and schooling (71% success fee) sectors
- Conversely, IT, know-how and telecoms (30% success fee) and retail (47% success fee) reported the bottom charges of profitable backup compromise
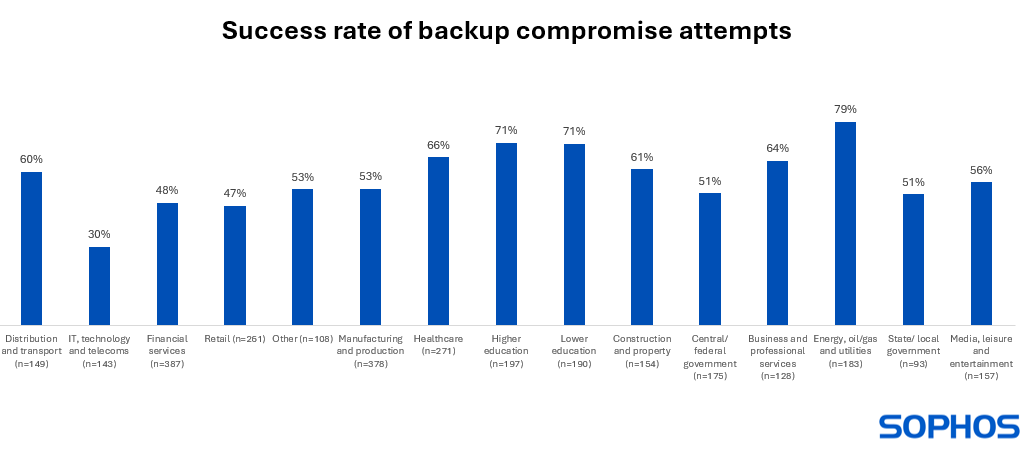
There are a number of attainable causes behind the differing success charges. It might be that IT, telecoms and know-how had stronger backup safety in place to begin with so was higher ready to withstand the assault. They might even be more practical at detecting and stopping tried compromise earlier than the attackers may succeed. Conversely, the power, oil/fuel and utilities sector could have skilled a better share of very superior assaults. Regardless of the trigger, the impression might be appreciable.
Studying 3: Ransom calls for and funds double when backups are compromised
Information encryption
Organizations whose backups had been compromised had been 63% extra prone to have knowledge encrypted than those who didn’t: 85% of organizations with compromised backups mentioned that the attackers had been in a position to encrypt their knowledge in contrast with 52% of these whose backups weren’t impacted. The upper encryption fee could also be indicative of weaker total cyber resilience which leaves organizations much less in a position to defend in opposition to all phases of the ransomware assault.
Ransom demand
Victims whose backups had been compromised obtained ransom calls for that had been, on common, greater than double that of these whose backups weren’t impacted, with the median ransom calls for coming in at $2.3M (backups compromised) and $1M (backups not compromised) respectively. It’s probably that adversaries really feel that they’re in a stronger place in the event that they compromise backups and so are in a position to demand a better cost.
Ransom cost fee
Organizations whose backups had been compromised had been nearly twice as prone to pay the ransom to get well encrypted knowledge than these whose backups weren’t impacted (67% vs. 36%).
Ransom cost quantity
The median ransom cost by organizations whose backups had been compromised was $2M, nearly double that of these whose backups remained intact ($1.062M). They had been additionally much less in a position to negotiate down the ransom cost, with these whose backups had been compromised paying, on common, 98% of the sum demanded. These whose backups weren’t compromised had been in a position to scale back the cost to 82% of the demand.
Studying 4: Ransomware restoration prices are 8X greater when backups are compromised
Not all ransomware assaults lead to a ransom being paid. Even once they do, ransom funds are simply a part of the general restoration prices when coping with a ransomware assault. Ransomware-led outages incessantly have a substantial impression on day-to-day enterprise transactions whereas the duty of restoring IT programs is usually advanced and costly.
The median total ransomware restoration prices for organizations whose backups had been compromised ($3M) got here in eight instances greater than that of organizations whose backups weren’t impacted ($375K). There are probably a number of causes behind this distinction, not least the extra work that’s sometimes wanted to revive from decrypted knowledge slightly than well-prepared backups. It might even be that weaker backup safety is indicative of much less sturdy defenses and better ensuing rebuilding work wanted.
These whose backups had been compromised additionally skilled significantly longer restoration time with simply 26% absolutely recovered inside per week in contrast with 46% of these whose backups weren’t impacted.
Suggestions
Backups are a key a part of a holistic cyber threat discount technique. In case your backups are accessible on-line, it’s best to assume that adversaries will discover them. Organizations can be smart to:
- Take common backups and retailer in a number of places. Be sure you add MFA (multi-factor authentication) to your cloud backup accounts to assist forestall attackers from gaining entry.
- Observe recovering from backups. The extra fluent you’re within the restoration course of, the faster and simpler it will likely be to get well from an assault.
- Safe your backups. Monitor for and reply to suspicious exercise round your backups as it could be an indicator that adversaries try to compromise them.
How Sophos will help
Sophos MDR: Over 500 consultants monitoring and defending your group
Sophos MDR is a 24/7 expert-led managed detection and response service that makes a speciality of stopping superior assaults that know-how alone can not forestall. It extends your IT/safety workforce with over 500 specialists who monitor your setting, detecting, investigating, and responding to suspicious actions and alerts.
Sophos MDR analysts leverage telemetry from the safety instruments you already use – together with your backup and restoration answer – to detect and neutralize assaults earlier than injury is completed. With a mean risk response time of simply 38 minutes, Sophos MDR works sooner than your subsequent risk.
Sophos XDR: Enabling IT groups to detect and reply to assaults
In-house groups can use Sophos XDR to get the visibility, insights, and instruments they should detect, examine, and reply to multi-stage threats, throughout all key assault vectors, within the shortest time. With Sophos XDR you may leverage telemetry out of your backup and restoration answer, in addition to your wider safety stack, to shortly see and reply to assaults.






